Using a Redirect Manager is like Hosting a Guestbook for Despicable people
I maintain several websites for my work at shift8 and I recently put in place a piece of software to record redirects on my site. Each time someone typed in a url like "http://shift8solutions.com/[REQUEST]" my redirect manager would record the attempt and the IP of the user. The goal was to find broken links and maybe, just maybe, understand if people expected a page to exist that I hadn't created.
How naive am I?
The true result was a log of all the bungled attempts to gain entry to my site. This made me happy because 1. I love data, 2. they did not succeed and 3. I learned a ton. Here is a breakdown of my wannabe hackers by country (top ten offenders):
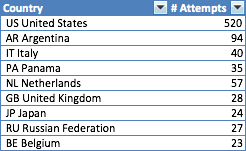
In general, the goal seemed to be direct access to phpmyadmin and various RSS feeds (that do not exist). There were also some very specific references to products that I do not own - most likely references to security issues in other software platforms. I recognized elements from Wordpress, Drupal, and Joomla. In general, it was fishing, not really hacking and it wasn't very sophisticated. I did learn a bit about what is visible to outsiders about my software choices.
For fun, using google tables, I made a heat map of the above data by country - Notice that most of these attempts were made from the US, but Argentina and most of Europe had activity as well.
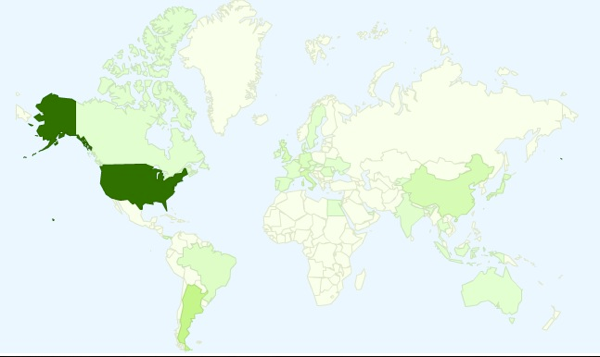
It's bizarre to look through these logs - there is far more information tracked, but it wouldn't be nice to post it. I guess I should say thanks to these guys - it made for an interesting bit of research and my site is stronger for it.
Thanks goons!
~ab